There are many industry discussions happening right now around Zero Trust models and why it may work for some organizations and not others. We’re using this industry term a bit “tongue-in-cheek” for our blog, but it does have some relevance when discussing secure, E2E encrypted collaboration platforms and how to deliver scalable solutions to enterprises who want fine-grain, administrative controls to manage their information and organizational needs.
The benefits and pitfalls about deploying enterprise-grade solutions are the policies around data governance and proper use of collaboration platforms. Once organizations have a fully vetted policy in place, the design aspects around proper use are more easily implemented.
A couple of important topics come into play when we work with our customers: Scale & Authorization. When we talk about Scale, it involves both capacity and building cross-collaborative networks. When we address Authorization, the questions and discussions lead to:
- “How do I provide a secure environment for our senior executives to discuss Board-level topics, such as:”
- M&A
- Fundraising
- Corporate Structures
- “How do I restrict information that’s only intended for internal audiences, like:”
- Human Resource
- Research & Development
- Crisis Management
- “I’d like to group users into certain information control profiles”
- Business Unit categorization
- “I have trusted 3rd parties I need to communicate with, how do we accomplish this?”
- Outside Corporate Counsel
- Incident Response
- Vendor Management
In order to address these topics, you must have a secure collaboration solution in place that allows strict policy enforcement – the ability to create tightly enforced Access Control Lists between users and networks. For example, sue@company.com is a Senior Director on the Incident Response (IR) team. She’s managing a high profile issue, but wants to validate the team’s results with a trusted 3rd party IR vendor/consultant. She doesn’t want to do this over open channels, but has a policy where she can invite the 3rd party to communicate over a secure channel as long as the 3rd party has been whitelisted for collaboration. Administrators would have the necessary functionality in place to easily allow Sue to only communicate outside her organization with that specific 3rd party.
On the flip side, your company has a customer facing organization – sales, for example – who work on proprietary and sensitive customer proposals. They will want to discuss these activities over secure channels with their prospects, and therefore may have an open policy to communicate outside their organization. You need to apply a single policy to the sales organization to communicate with other users/encrypted endpoints.
Here’s a high-level example describing secure communication inside or outside your organization:
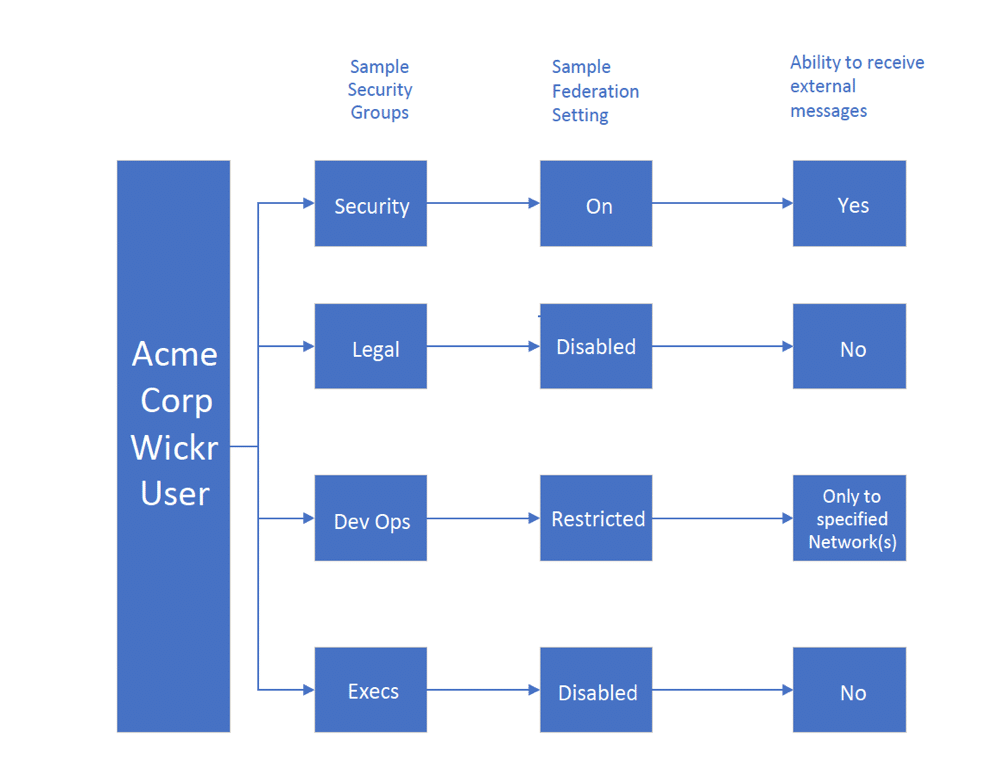
While establishing a system architecture and placing users in the proper security groups, some organizations may want to integrate additional controls like Data Loss Protection, Active Directory/LDAP or communications archiving for eDiscovery/Risk/Auditing – all of these capabilities should be part of your overall plan when designing and deploying your E2E, encrypted collaboration solution.
In the end, Zero Trust is not a blunt object – it should be flexible enough to create specific processes for established policies and needs across your organization.
